home
Privileged Access
What Is Privileged Access Management (PAM)?
Organizations implement privileged access management (PAM) to protect against the threats posed by credential theft and privilege misuse. PAM refers to a comprehensive cybersecurity strategy – comprising people, processes and technology – to control, monitor, secure and audit all human and non-human privileged identities and activities across an enterprise IT environment.
Sometimes referred to as privileged identity management (PIM) or privileged access security (PAS), PAM is grounded in the principle of least privilege, wherein users only receive the minimum levels of access required to perform their job functions. The principle of least privilege is widely considered to be a cybersecurity best practice and is a fundamental step in protecting privileged access to high-value data and assets. By enforcing the principle of least privilege, organizations can reduce the attack surface and mitigate the risk from malicious insiders or external cyber attacks that can lead to costly data breaches.
Key Privileged Access Management Challenges
Organizations face a number of challenges protecting, controlling and monitoring privileged access including:
- Managing account credentials: Many IT organizations rely on manually intensive, error-prone administrative processes to rotate and update privileged credentials. This can be an inefficient and costly approach.
- Tracking privileged activity: Many enterprises cannot centrally monitor and control privileged sessions, exposing the business to cybersecurity threats and compliance violations.
- Monitoring and analyzing threats: Many organizations lack comprehensive threat analysis tools and are unable to proactively identify suspicious activities and remediate security incidents.
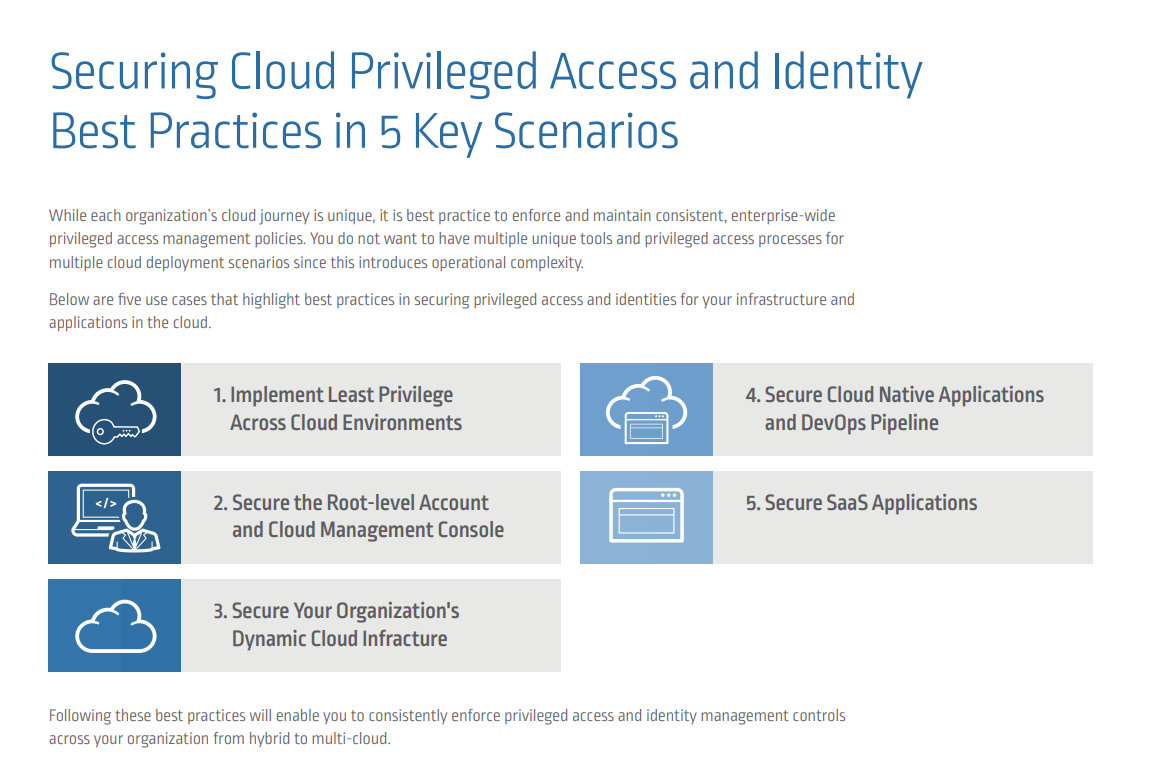
- Controlling Privileged User Access: Organizations often struggle to effectively control privileged user access to cloud platforms (Infrastructure as a Service and Platform as a Service), Software as a Service (SaaS) applications, social media and more, creating compliance risks and operational complexity.
- Protecting Windows domain controllers: Cyber attackers can exploit vulnerabilities in the Kerberos authentication protocol to impersonate authorized users and gain access to critical IT resources and confidential data.
ENFORCE LEAST PRIVILEGE
Apply least privilege security controls across all identities, devices and apps, from the endpoint to the cloud.
Defend Against Attacks
Enable the Digital Business
Satisfy Audit and Compliance
STOP ATTACKERS IN THEIR TRACKS
CyberArk Privileged Access Management solutions address a wide range of use cases to secure privileged credentials and secrets wherever they exist: on-premises, in the cloud, and anywhere in between.
Privileged Access Manager
Cloud Entitlements Manager
Endpoint Privilege Manager
Vendor Privileged Access Manager
For more information, visit: https://www.cyberark.com/products/privileged-access/



