home
Access Management
CyberArk Blueprint Helps Reduce Identity Security Risks
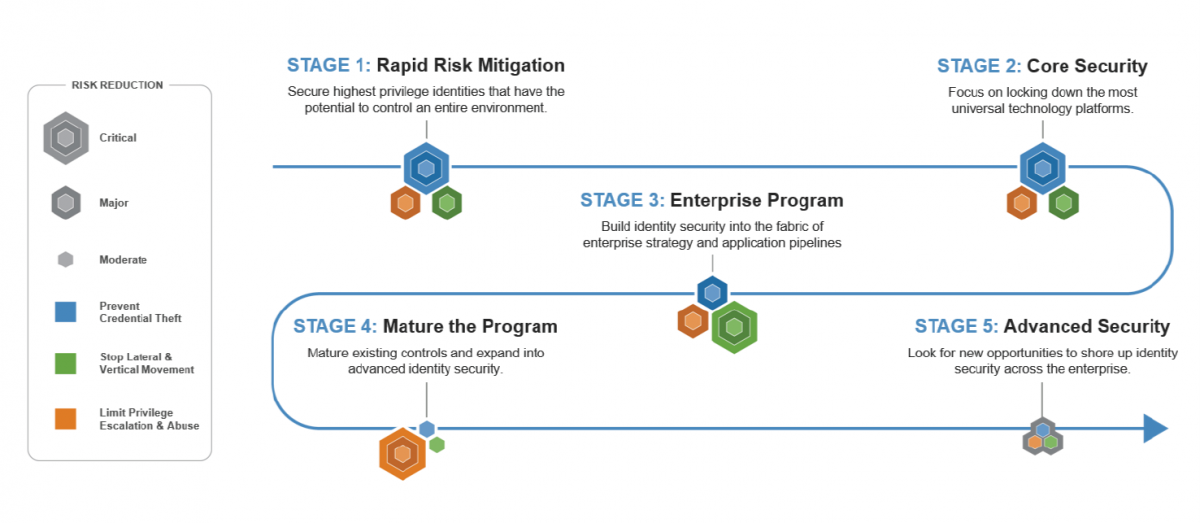
CyberArk has developed a prescriptive blueprint framework to help organizations establish and evolve an effective Identity Security program. The CyberArk Blueprint for Identity Security Success (or CyberArk Blueprint for short) is designed to defend against three common attack chain stages used to steal data and wreak havoc. Simple, yet comprehensive, the CyberArk Blueprint provides a prioritized, phased security framework that closely aligns Identity Security initiatives with potential risk reduction, helping organizations address their greatest liabilities as quickly as possible. It should be used as a tool to help guide your own Identity Security program roadmap development, in combination with your current state, internal priorities and desired business outcomes.
The CyberArk Blueprint was built with contemporary organizations and extensibility in mind. It prescribes Identity Security controls and best practices for organizations using conventional on-premises infrastructure and software development methods, as well as for organizations embarking on digital transformation projects such as migrating infrastructure to the cloud, adopting CI/CD practices, optimizing processes through robotic process automation or implementing SaaS solutions for business-critical applications.
The CyberArk Blueprint reflects the combined knowledge and experience of CyberArk’s global Sales, Sales Engineering, Security Services and Customer Success organizations. As a recognized leader, CyberArk is uniquely positioned to deliver a thorough and effective Identity Security plan:
- CyberArk solutions are trusted by 6,300+ customers, including more than 50% of the Fortune 500, across a wide range of industries including financial services, insurance, manufacturing, healthcare and tech.
- CyberArk’s Remediation and Red Team have been front and center in helping companies recover from some of the largest breaches of the 21st century. Additionally, CyberArk draws on the insights of its Threat Research and Innovation Lab.
- CyberArk Security Services and Customer Success organizations have decades of real-world implementation and support experience, and have a detailed, first-hand understanding of the risks present within human and non-human identities and best practices.
- Leading research and advisory firms recognize CyberArk as a privileged access management leader for both completeness of vision and ability to execute.
EMPOWER WITH ACCESS MANAGEMENT
Identity is the new battleground for security. With CyberArk’s Access Management solutions, you can let users in – while using AI to help keep threats out.
Drive Operational Efficiencies
Defend Against Attacks
Enable the Digital Business
Three Guiding Principles for Identity Security Success
While every organization’s IT environment is unique, perpetrators can attack virtually any business by following well established steps in the attack chain:
- Gain unauthorized access to privileged identities
- Traverse the network looking for high-value targets
- Use elevated privileges to steal confidential information or disrupt services.
The CyberArk Blueprint helps organizations strengthen their security posture by thinking like an attacker and defending against the three techniques adversaries typically use to access privileged identities, steal data and take down systems.
More specifically, the CyberArk Blueprint for Identity Security Success is based on three guiding principles:
- Prevent credential theft
- Stop lateral and vertical movement
- Limit privilege escalation and abuse
The Blueprint is designed to protect any customer environment, strengthening Identity Security for on-premises, cloud or hybrid infrastructure. It lays out a pragmatic, risk-based implementation plan that introduces security controls in stages, helping businesses address their most pressing needs in the short-term, while providing a long-term plan to address the more advanced security use cases.
For more information, visit: https://www.cyberark.com/products/access-management/



